Security Integration
Integrate ConfigSeeder® with OIDC, SAML, or pre-authentication based on HTTP headers into the existing security infrastructure.
Security integrations offered by ConfigSeeder®
ConfigSeeder® offers a secure way to manage your configuration data.
One important element of the security concept is that the configuration values are stored in an encrypted form.
Another is that configuration values marked as secured are only displayed on request.
This is true even for users who are authorized to view these saved configuration values.
These security elements are only as good as the mechanisms that are used for authentication and authorizing the users.
With OIDC and SAML, ConfigSeeder® offers two well-established standards for security integration. With pre-authentication based on HTTP headers, there is a third way for integrating ConfigSeeder® into the existing security infrastructure.
OIDC
Use an existing OpenID Connect installation like Keycloak, Octa, or even ADFS as Identity Provider for ConfigSeeder. Metadata like username, email, … and roles can be transported in the token.
Find more details in the system documentation.
SAML
Use an existing SAMLv2 Identity Provider for security integration. Like in OIDC, the metadata like username, email, … and roles can be transported in the token.
Find more details in the system documentation.
Pre-Authentication based on HTTP Headers
For scenarios where OIDC and SAML can’t be used, ConfigSeeder® can be configured to trust pre-authenticated users based on HTTP headers. This scenario is often seen when users accessing services are identified by a web application firewall like Airlock or similar.
Find more details in the system documentation.
Managing privileges
With any of the supported security integration mechanisms, permissions can be managed in different variants. Each of the variants has different properties and leads to a different degree of coupling between ConfigSeeder® and the identity provider:
| Variant | Coupling | Description |
|---|---|---|
| ConfigSeeder® managed roles | no coupling | The IDP is only used for authentication. The assignment of Roles is done in ConfigSeeder®.
|
| IDP managed roles | low coupling | The IDP is used for authentication and authorization.
|
| IDP managed permissions | high coupling | The ConfigSeeder® specific permissions are handled in the IDP:
|
We recommend to follow the IDP managed roles approach:
- Define the roles that will be used
- Create the roles in ConfigSeeder®, assign the required function permissions and data permissions
- Assign the roles with the IDP to the users
Examples for assigning permissions
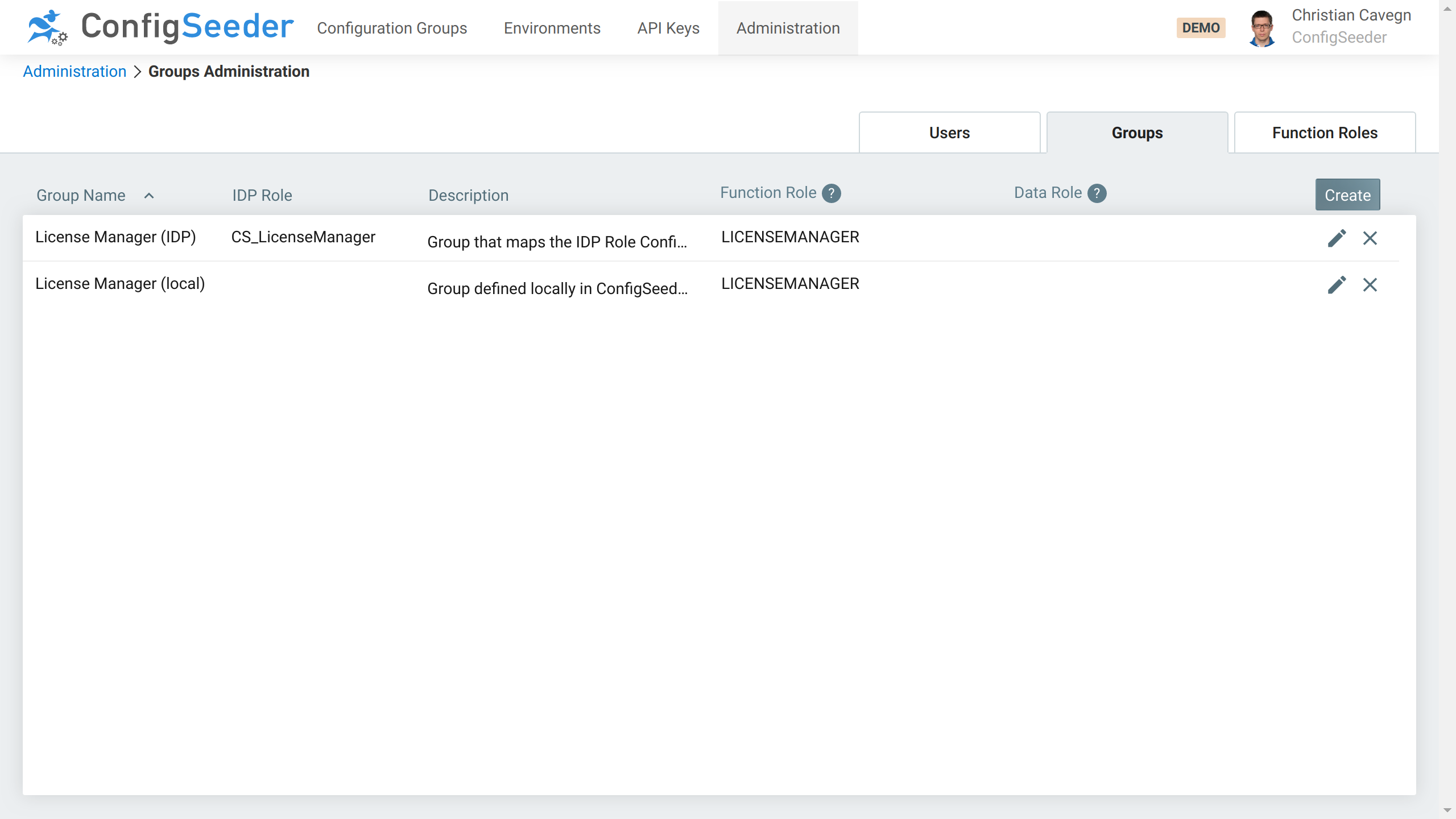
The following screenshot shows two groups that both grant the LICENSEMANAGER role. The first group maps the role CS_LicenseManager provided by the IDP to LICENSEMANAGER, the second role doesn’t know an IDP role and is meant to be assigned manually.
The following screenshot shows the manual assignment of the role License Manager (local) to the user developer.
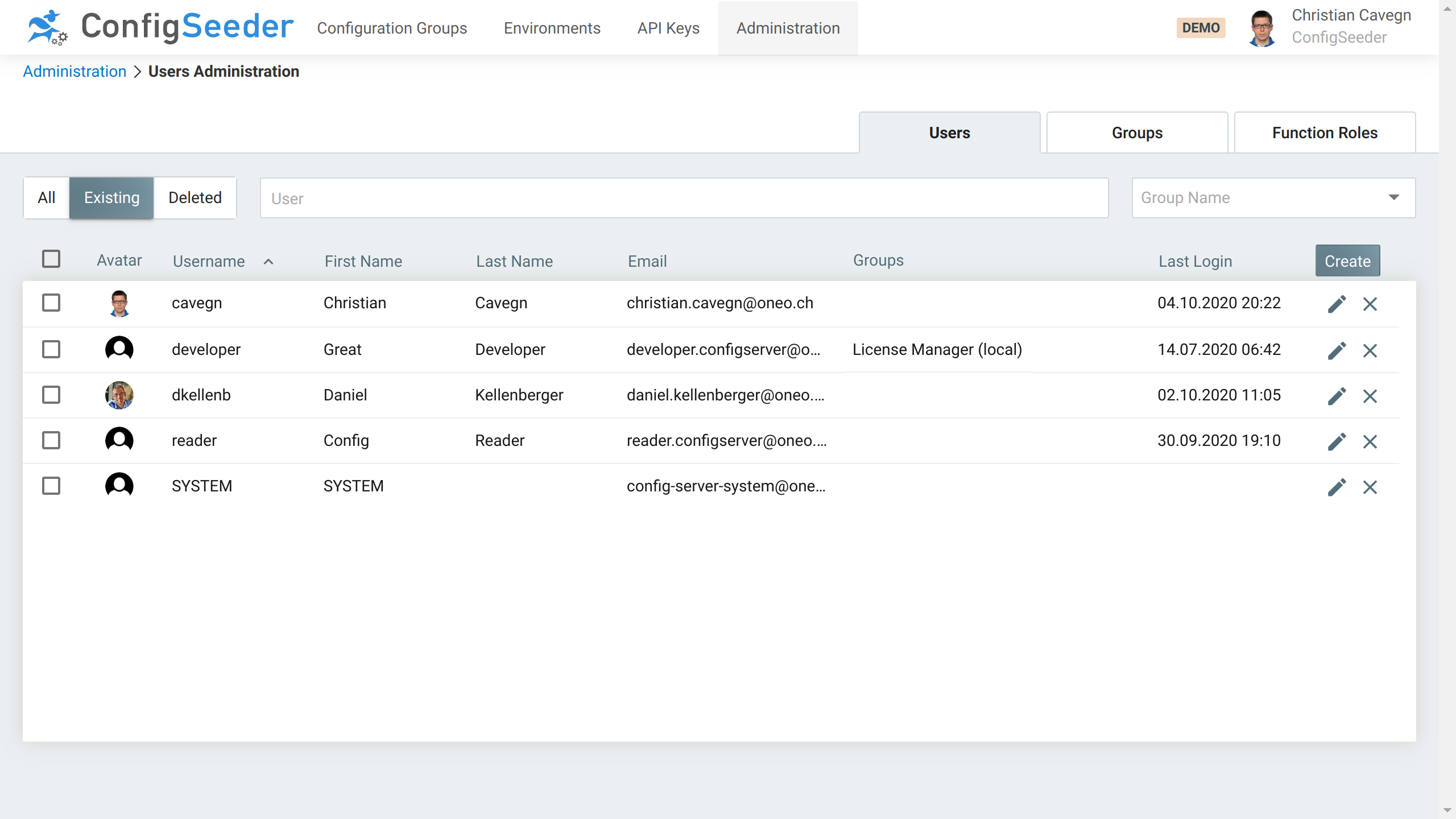
All users to whom the IDP assigns the role CS_LicenseManager, receive the permissions granted by the group License Manager (IDP) automatically. Therefore, this group isn’t manually assigned to any user.

