Application Configuration Management
What is Application Configuration Management?
Under application configuration management we understand the process of maintaining the configuration data for all applications.
Nearly every application (or microservice or deployment) requires some configuration:
- Access to a database (URL, connection parameters, username, password)
- Access to downstream services (URL, connection parameters, credentials)
- Other configuration parameters like ports, log level, …
- Security relevant objects like trust stores and key stores
Under application configuration management we understand the sum of this configuration data.
Different frameworks implement different concepts to configure an application. For example:
Different runtime environments use different standards:
- An application running on a virtual machine (VM) is usually configured with configuration files, startup parameters or environment variables.
- When running an application in Kubernetes or Openshift, the configuration is usually done with ConfigMaps and Secrets. (Of course, the information stored inside these objects are injected as files or environment variables into the containers)
Common Challenges
Some of the most common challenges in application configuration management are multiple environments, access management, distribution over many repositories, reuse of configuration data as well as the support of different runtime environments.
Let’s take a look at those five common challenges in detail (some more are described in our article Wy should you consider ConfigSeeder®):
- Multiple environments – Usually there is not only a production environment but also one, or many test environments. Some configuration data may be identical for all environments, most will be different (the URL of a downstream service will be different for the test and production environment).
- Access management – Some configuration data like a log level or information about ports is not critical. Other information like passwords, tokens, private keys and similar must be protected. However, it should be easy for authorized co-workers to also access confidential information.
- Distributed configuration – If no application configuration management system is used, the configuration data is usually stored in the source control repository in which the application is developed. From a release or application manager’s point of view, the application configuration is therefore distributed over many repositories.
- Reuse of configuration data – Some of this configuration data may be shared between many applications (like URLs of downstream services, default log level, trust stores, …) other configuration objects like key stores should only be used by one application.
- Support different runtime environments – Newly build applications may run in Kubernetes, some older applications run directly on a VM. There are different technologies and OS. Configuration data must be made available for all runtime environments and technologies.
How can ConfigSeeder® help?
ConfigSeeder® securely manages and stores your application configuration at a central place. It can hold the configuration data for many applications and environments and support for reusing configuration data is built-in. ConfigSeeder® also has a fine-grained access control system and integrates with existing security infrastructure (OIDC, SAML, and even HTTP pre-authentication).
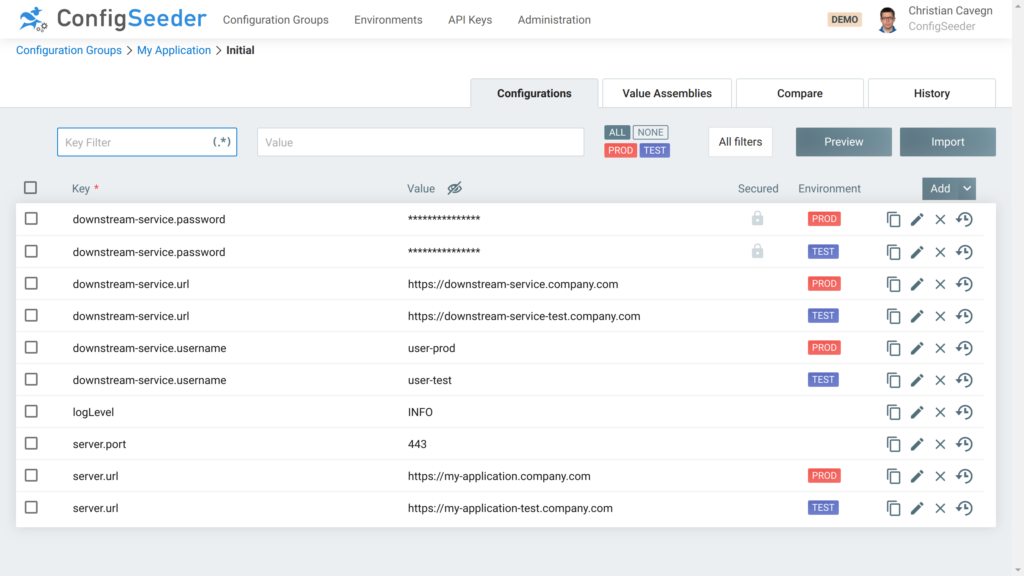
ConfigSeeder® offers integration for different runtime environments. Have a look at
- Ecosystem for a description of all our components
- SpringBoot and Eclipse Microprofile integration
- Kubernetes Connector and Kubernetes Connector in a multi-cluster setup for ConfigSeeder® Kubernetes Integration.
- ConfigSeeder® & Linux/Windows integration
- Ansible Integration
Get more information about how ConfigSeeder® works and have a look at our features to see what ConfigSeeder® can do to improve your application configuration management.
In short, ConfigSeeder® will bring the management of application configuration data up to the next level.

